Random SSH Agent Tricks
Posted Oct 26 2017, 15:58 by William Shallum [updated Oct 26 2017, 15:59]
If you have a Linux Server somewhere, you typically access it using SSH. If your server is accessible over the Internet, the log files will tell you that it receives hundreds to thousands of brute force login attempts per day.
Sep 10 04:19:59 vm auth.info sshd[8360]: Invalid user ubnt from
1.54.xx.yy
Sep 10 04:19:59 vm auth.info sshd[8360]: input_userauth_request:
invalid user ubnt [preauth]
Sep 10 04:19:59 vm auth.err sshd[8360]: error: Received disconnect from
1.54.xx.yy port 57526:3: com.jcraft.jsch.JSchException: Auth fail
[preauth]
Sep 10 04:19:59 vm auth.info sshd[8360]: Disconnected from 1.54.xx.yy
port 57526 [preauth]
Sep 10 04:20:19 vm auth.info sshd[8362]: Invalid user support from
1.54.xx.yy
Sep 10 04:20:19 vm auth.info sshd[8362]: input_userauth_request:
invalid user support [preauth]
Sep 10 04:20:19 vm auth.err sshd[8362]: error: Received disconnect from
1.54.xx.yy port 58807:3: com.jcraft.jsch.JSchException: Auth fail
[preauth]This means “12345” is not a good root password. Actually you probably want to log in using a key instead, as that’s a lot harder to brute force than “12345”. Feel free[1] to use “12345” for your local private key password if you miss it.
So, like any security-minded individual you protect your private keys on disk with a password. The problem with this is you have to type the password to decrypt the key every time you want to use it. The ssh-agent is a program that will stay in memory, and hold the decrypted private key for you, so it can be used by your SSH processes.
So everything is OK, you enter the password once, and the agent has the decrypted key. Your future ssh sessions automatically contact the agent to get the keys.
1. Do not use the agent from GNOME Keyring
user@vm:~$ ssh-add -l
2048 30:cb:fb:28:09:69:da:22:3a:12:4a:0a:8a:03:3b:f0 user@vm (RSA)
user@vm:~$ ssh-add -D
All identities removed.
user@vm:~$ ssh-add -l
2048 30:cb:fb:28:09:69:da:22:3a:12:4a:0a:8a:03:3b:f0 user@vm (RSA)
user@vm:~$ ssh-add ~/.ssh/id_ecdsa
Error reading response length from authentication socket.
Could not add identity: /home/user/.ssh/id_ecdsa
user@vm:~$ ssh-add ~/.ssh/id_ed25519
Error reading response length from authentication socket.
Could not add identity: /home/user/.ssh/id_ed25519
user@vm:~$ echo $SSH_AUTH_SOCK
/run/user/1000/keyring-aUXdpV/sshThe agent from GNOME keyring cannot remove a passwordless default key, it cannot handle key types other than DSA & RSA, it also does not support the tricks here. On Ubuntu 14.04 with Unity, run gnome-session-properties, uncheck the SSH Agent, and restart the desktop session.
2. Add a lifetime to the keys in your agent
Ideally you would remove keys after you finish using them. This reduces the possibility that someone else will use them. If you often don’t remember to remove the keys, why not let the computer do it for you?
user@vm:~$ ssh-add -t 30 ~/.ssh/id_rsa; ssh-add -l ; sleep 31; ssh-add
-l
Identity added: /home/user/.ssh/id_rsa (/home/user/.ssh/id_rsa)
Lifetime set to 30 seconds
2048
30:cb:fb:28:09:69:da:22:3a:12:4a:0a:8a:03:3b:f0 /home/user/.ssh/id_rsa
(RSA)
The agent has no identities.By using the -t option, keys will be automatically removed after the time has passed. The time unit is seconds by default, but you can also use “10m” (minutes), “10h” (hours), “10d” (days) and combinations like “1h30m” or “10d10h10m10s”[2].
3. Prompt for confirmation when the key is used
Let’s say you have your keys in the agent and ready to use. How do you know that you are the only one using them? Anyone who logs in as root or the same user will be able to connect to the agent’s socket and request keys. One way is to make the agent prompt for confirmation for each use with the -c option.
This probably works better with agent forwarding as local root can probably do other, nastier things to the agent process.
user@vm:~/.ssh$ ssh-add -c ~/.ssh/id_ecdsa.priv
Identity added: /home/user/.ssh/id_ecdsa.priv
(/home/user/.ssh/id_ecdsa.priv)
The user must confirm each use of the keyAfterwards, if you try to use it, a box like this pops up:
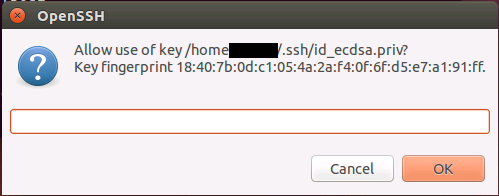
The askpass prompt for confirmation. The textbox does nothing, just click OK or Cancel.
If you press OK, the agent allows use of the key and the connection attempt succeeds. If you press Cancel, the agent will reject the request as seen below:
user@vm:~/.ssh$ ssh localhost
Agent admitted failure to sign using the key.
user@localhost's password:4. Lock your agent
The ssh-agent can be locked with a password. The agent must be unlocked for the keys inside to be usable again.
user@vm:~$ ssh-add
Enter passphrase for /home/user/.ssh/id_rsa:
Identity added: /home/user/.ssh/id_rsa (/home/user/.ssh/id_rsa)
user@vm:~$ ssh-add -l
4096
00:11:22:33:44:55:66:77:88:99:aa:bb:cc:dd:ee:ff /home/user/.ssh/id_rsa
(RSA)
user@vm:~$ ssh-add -x
Enter lock password:
Again:
Agent locked.
user@vm:~$ ssh-add -l
The agent has no identities.
user@vm:~$ ssh-add -X
Enter lock password:
Agent unlocked.
user@vm:~$ ssh-add -l
4096
00:11:22:33:44:55:66:77:88:99:aa:bb:cc:dd:ee:ff /home/user/.ssh/id_rsa
(RSA)[1]: don’t do this.
[2]: See sshd_config manual page, TIME FORMATS section.